
Net Protector Tablet Security
Our Research Lab has launched new Net Protector Tablet Security App for the Android Tablets
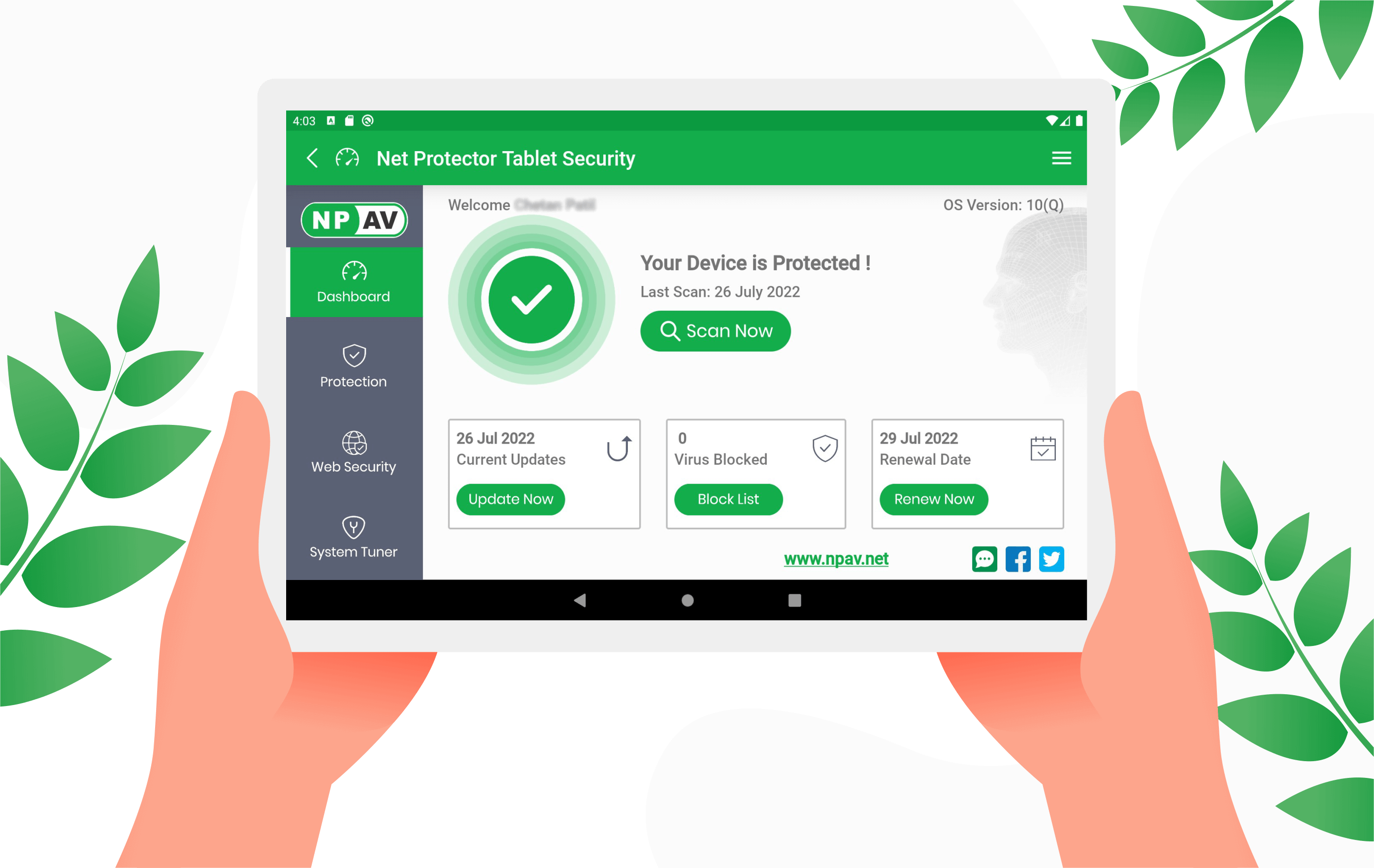
Net Protector Tablet Security
- Useful to clean Viruses, Worm Dialers, Trojans and Other Malicious Activities from Tablet device and attached SD Card.
- Any Application that you install is first scanned by the resident Net Protector Tablet Security Shield.
- All required security is provided to keep your Tablet safe and secure in an easy-to-use Tablet Security Application.

Features of Tablet Security

Scan
It is used to scan all the files present on your device to detect whether any file contains any malicious programming that will be harmful to your device or it is clear to use. After clicking on the Scan button it will start completing mobile scanning. Users can also able abort a scanning by pressing the abort button. After completion of the scanning process, it will display the scan summary.

Update
Provides the Latest Updates in Apps.

Schedule Scan
Schedule your Scan Timing as per your need (Daily / Weekly).

Secure Payment
Secure your payment information while making payments anywhere.

Weak Setting Scan
The settings like the Developer option, and USB Debugging may be harmful to your device. This option scans and disables weak settings.

Secure QR Scanner
You can check the data provided through QR codes, whether these data are harmful or safe before opening it on the web browser or on other apps.

Apps Usage
Apps Usage shows the summary of the total time spent by you on different apps.

App Manager
This feature lists all apps installed by users with the app size. User can uninstall unwanted apps to optimize memory, and improve the device speed.

Phone Booster
It boosts your device by suspending the unused apps or services running unnecessarily on the device.

Privacy Control
It is used to check what permissions are used by apps installed on your device. Some malicious apps take unnecessary permissions that won't be needed to work and can leak your data or monitor your device. So you can find the list of permissions used by apps and can handle it here. For this, 2 categories are app lists on the basis of permissions they used and permissions list used by any app.

Space Analyser
It gives information about available or used spaces in internal and external memory for memory management. It categorizes the whole space available according to file type e.g. Images, Videos, Documents, Apps, or Downloads and sorting is available for all the files. Users can get the explicit path of a file/directory.

Duplicate File Fixer
It finds all the file that appears more than once on the device and provides the option to clear multiple appearances of type of file. It is also categorized on the basis of file types. Users are often able to find such files, but it captures memory unnecessarily.

System Information
Easy listing of hardware and software available in the system here.

My Account
If a user enables this option, all the hardware and software-related details of all the devices associated with the same user will be available in the same place on the cloud. Users can access it and use features to manipulate it remotely using our app "my account" or web portal "myaccount.npav.net".

Vulnerable Apps
This feature finds the malicious or unverified(not verified from the play store)application that may be harmful to your device and provides an option to delete it.